In 2023, the UK government published two reports that were important for the nonprofit sector – the NCSC’s Cyber Threat Report: UK Charity Sector, and the Cyber Security Breaches Survey. These reports share common themes around the importance of authentication, security updates, updating firewalls, and crucially, Cyber Essentials as a useful framework to help protect your organisation against cyber attacks.
While some may already be familiar with the Cyber Essentials certification, many charities will be considering it for the first time, or looking to renew their certification and ensure they are well prepared.
Smartdesc are an accredited Cyber Essentials Assessment Body, taking charities of all sizes through the process of getting certified for both Cyber Essentials, and Cyber Essentials Plus. We are 100% dedicated to the nonprofit sector, so we understand how nonprofit organisations work too!
In this article, we guide you through our recommendations on how to approach your Cyber Essentials journey. based on our experience of issuing the accreditation and managing the process for numerous nonprofits.
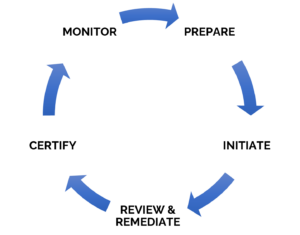
Preparation is key. Know your Assets and Document them!
Any device that your organisation uses to connect to applications and services such as email, office documents, files, customer data – through laptops, desktops, mobile phones or tablets – should be documented or tracked so that you know which devices need appropriate security updates.
Furthermore, if staff connect to a server – either based in your office or to a virtual server via a VPN – you need to note this and the operating system (and for virtual servers, the hypervisor details of that virtual server).
You will then need to know the software and applications that your staff are authorised to use (also known as software-as-a-service). The way that we ask our customers to think about this is to categorise each department and think about the applications they use.
For example, what do HR use for payroll, holidays, personnel file management? What do the Accounts team use for banking, donations, expenses? What Customer Relationship Management (CRM) tool do you use? Think about all the applications you use that require a password or other authentication.
Not knowing this information could lead to an automatic failure of your Cyber Essentials Assessment. Therefore, if any of this is managed by outsourced IT support, we highly advise liaising with them beforehand. Find out what equipment in the office is used to connect to the internet. Also, whether the equipment receives security updates or if you need to update the router/hub/modem to a newer version that receives security updates by the manufacturer.
Nowadays it is deemed normal practice to use a mobile phone at work – either supplied by the organisation or your personal device – to access systems such as company email. Do you know whether staff are updating the operating system of their devices to the latest version? Or is this rolled out automatically via a dedicated support provider? If your staff use their personal devices, you may want to consider implementing a Bring Your Own Device (BYOD) policy that states the obligations of staff to carry out security updates within a set timeframe (usually within 2 weeks of the update being released). Otherwise consider rolling out company-issued devices that you can control and update remotely.
Initiate
Once you have what established your IT assets, you are in a much better position to answer the questions required for the certification. Contact your certification body and they will work with you to go through the questions. If you know the assets you hold and what is on them, then this will be a fairly straightforward process. There may still be questions that you cannot answer in a compliant manner, but these remediations should be manageable if you have covered the essential components in the initial meeting.
Remediate & Review
We mentioned that there might be questions in the initial meeting that are classed as “non-compliant”. However, you should aim to answer any question that might otherwise lead to an automatic failure (and you will often overcome any “automatic failure” questions by doing the preparation before you move to the initiation phase). Cyber Essentials allows for up to two “non-compliances”. Your Certification Body will work with you to explain what the non-compliances mean and your options in terms of remediations.
Remember that Cyber Essentials is a point-in-time exercise – if you start the assessment but do not complete all the responses within an acceptable timeframe, you will have to go back and update some of the answers in your initial meeting as they may be out of date by the time of submission. Therefore, reviewing your responses before moving to the certification stage is key, otherwise it may delay the issuance of your certification.
Certify!
The most challenging part of the assessment has been covered in the preparation, initiation and remediation phases. Your Certification Body will then upload your assessment and they should be able to issue you with your Cyber Essentials Basic certification.
Once you’ve received your report with certificate ID, you have a three-month window to upgrade this from Basic to Plus. We can advise you on the process for this and guide you through it.
Monitor
Whether you decide to end the process at the Cyber Essentials Basic stage, upgrade to Cyber Essentials Plus, or plan to annually renew your certificate, monitoring your hardware, software, applications, and cyber hygiene is vital. It is a lot easier than forgetting about them for another year and having to prepare with the same level of detail as the first time!
Get in touch
At Smartdesc, we are a licensed Cyber Essentials Certification Body and have helped dozens of nonprofits achieve certification quickly and easily. We will guide you through every step of the process and are always on hand to help – whether you are just considering options or actively looking to attain the certification. Get in touch with us here.